How good are the security measures you have in place?
Take this quick 10 question quiz to see if you’re doing all you can to keep your data safe. Learn why these best practices are integral to the success of your IT operations.
- 1. Do you have a cybersecurity policy with an adequate level of coverage?
Excellent! That’s a very important piece of protection for your business. Have you reviewed it recently to ensure you don’t have any coverage gaps (such as cyber war exclusions)?
Even with the best cybersecurity defenses in place, organizations can fall victim to a cyberattack. Cyber insurance is designed to help businesses with the financial burden of returning to normal operations in the aftermath of a cyber incident. Types of coverage vary – first-party loss, first-party expenses, and third-party liability, each with specific parameters. You’ll want to find the policy that’s the right fit to protect your business and accelerate recovery in the event of an attack.
- 2. Do your frontline/after-hours technicians know your emergency escalation procedures?
Great! It never hurts to review those procedures from time to time with the team to ensure everyone’s ready for the unexpected to happen.
Onboarding new technicians is an ongoing process. Why not set aside some time to ensure everyone’s on the same page and ready to go?
Unfortunately, it’s not a matter of IF things will go wrong, it’s a matter of WHEN. Empowering and training your team on how to respond to an emergency is critical to the success of your business.
- 3. Have you tested your team with a drill?
You’re on top of it! Kudos!
According to a Harvard Business Review study, “firms that ‘slowed down to speed up’ improved their top and bottom lines, averaging 40% higher sales and 52% higher operating profits over a three-year period.” Teams that take the time to get things right, rather than plowing ahead full steam, are more successful. Running a drill with your team ensures you have strategic alignment around your security initiatives and can expose flaws in the system before you’re in a position where those errors can cause real damage to your business.
- 4. Is your Incident Response & Crisis Management Plan up to date?
Fantastic! If you want to check your plan against some helpful tips, you can find those here.
It’s important to have a plan prepared for when something goes wrong because it helps you take control of the situation, and reduce the impact on your business. Here are some helpful tips to get started.
- 5. When did you last run a test restore?
There isn’t a concrete rule about how often you should check your backups and run a test restore. The key is to do it at a frequency that makes sense for your business and to always do it for a new environment (such as when you’re using a new cloud storage provider).
- 6. I have a regular review cycle where I check in with my customers about what needs to be backed up _____.
That’s awesome that you’re checking in regularly with your clients to ensure the right data is getting backed up, and nothing is getting missed.
That’s awesome that you’re checking in regularly with your clients to ensure the right data is getting backed up, and nothing is getting missed.
Things change inside businesses all the time. Ensuring that the right data is backed up, and nothing is getting missed, is the foundation to your success. (Have they added another drive or an employee that they haven’t thought to tell you about?) When something goes wrong, you want to be confident that everything the client needs will be included in the restore.
Things change inside businesses all the time. Ensuring that the right data is backed up, and nothing is getting missed, is the foundation to your success. (Have they added another drive or an employee that they haven’t thought to tell you about?) When something goes wrong, you want to be confident that everything the client needs will be included in the restore.
- 7. Do you use strong passwords?
Gold star! Your mom would be so proud.
We recommend using randomly generated passwords with a variety of special characters, capital and lowercase letters, and numbers. The most secure way to keep things organized is to utilize password manager software, which encrypts the passwords.
Implementing an "insider threat mitigation" strategy is also very important. When an employee leaves the organization or is dismissed, it's crucial to change passwords that person had access to in order to prevent tampering or sabotage.
No time like the present to get that set up. Yes, right now. We’ll wait.
We recommend using randomly generated passwords with a variety of special characters, capital and lowercase letters, and numbers. The most secure way to keep things organized is to utilize password manager software, which encrypts the passwords.
Implementing an "insider threat mitigation" strategy is also very important. When an employee leaves the organization or is dismissed, it's crucial to change passwords that person had access to in order to prevent tampering or sabotage.
- 8. Have you updated all default credentials?
That’s great that you’re taking care of your customers who work in healthcare or need to respect data sovereignty regulations in the EU.
Ahh mate…. This is my disappointed face. You know better than that.
- 9. I have different levels of permissions set up to protect end users and mitigate insider threat risk (such as a disgruntled employee sabotaging your system).
Excellent – setting tiers of permissions helps protect your business from both unexpected and, in some cases, unintentional risk and is therefore highly recommended.
We all want to believe the best of the people around us, however it’s important to protect your business from all sorts of risks, including unexpected ones. Setting tiers of permission levels protects the business from intentional and, to a certain extent, unintentional mistakes – and is therefore highly recommended.
- 10. My network is secure. I have anti-malware software in place. I’ve installed software updates. And I’ve hardened remote access.
Fantastic! You’re all over this!
These are important areas to address to keep your business protected and secure.
Congrats!! You’re a security whiz!
A critical part of your any disaster recovery and business continuity strategy is having a secure backup platform in place. Backups are your last stand when a threat penetrates your defenses.
If you aren’t totally satisfied with your current backup platform, or just like trying what else is out there to satisfy your curiosity, test drive Comet Backup with our free 30-day trial!
Now you have some areas where you can put a little time into increasing the security of your business to ensure you have a great disaster recovery and business continuity strategy in place!
A critical part of your any disaster recovery and business continuity strategy is having a secure backup platform in place. Backups are your last stand when a threat penetrates your defenses.
If you aren’t totally satisfied with your current backup platform, or just like trying what else is out there to satisfy your curiosity, test drive Comet Backup with our free 30-day trial!
If you want your backups
FAST
SECURE
ENCRYPTED
DEDUPLICATED
INCREMENTAL FOREVER
AFFORDABLE
CONFIGURABLE
RELIABLE
test drive Comet Backup





Configurable data protection for
Windows
Linux
macOS
Microsoft 365
Files & Folders
Databases
Servers
Emails & Calendars
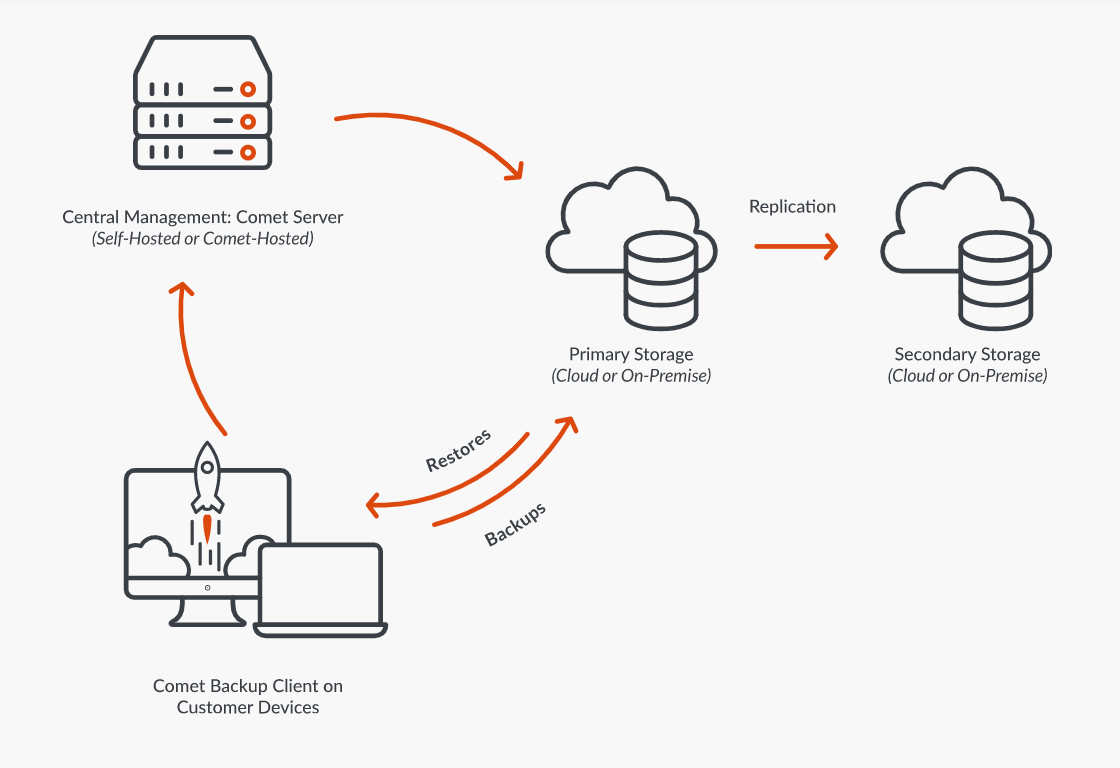
How it Works

Client-ServerModel
Efficiently manage backups for all your users in one place with our fast, secure backup platform. Save time by adding users and running upgrades in bulk.

Self-Hosted orComet-Hosted
Self-host a Comet Management Console or Storage Gateway in your own physical or virtual environment.Or we can host and manage one for you on a private AWS cloud.

ProfitablePricing
Grow your bottom line with our simple, per-device pricing.No contracts. Support, updates, replication, and re-branding are all free.

You’re inControl
You choose your backup destination (local or cloud), server location, configuration and setup.
Centralized Management with Comet’s Intuitive User Interface
Your data is secure, easily discoverable and always accessible
Start Running Backups and Restores
in Less than 15 Minutes
30-Day Free Trial • No Credit Card Required • Easy Deployment
Technology Benefits
Modern ‘Chunking’ technology powers Comet, making us faster than our competitors.
Client-side Deduplication
Comet has fast, bandwidth-efficient backups as deduplication is client-side, saving storage space.
No Full Re-uploads
After the first backup, you’ll never have to re-upload the full file again.
Incremental Forever
Your oldest backup can restore just as fast as your most recent. No need for differentials or delta-merging.
Compressed and Encrypted
During backup, transit and rest. The only time it is unencrypted is during a restore.
Packed with All the Features IT Providers Need
Lightweight Client
(Starting at less than 20MB)
Deduplication
Free Support
White Label Software
Built in SSL Support
Comprehensive API
Silent Install
No Java or .NET
Support for Code Signing
Still on the fence?
Let us answer some of your most commonly asked questions.
Can I get a price estimate for my business?
+Comet’s affordable, per-device pricing scales inline with your business growth. No contracts. Support, updates, replication, and re-branding are all free.
We believe in pricing transparency. Calculate your monthly usage with our handy Backup Cost Calculator.
Can I offer free demos and trials of Comet to my customers?
+Yes, Comet offers a 14-day Customer guarantee. This applies to any new user account you create, allowing you to demonstrate the service to your customer. Simply delete a user account within 14 days of creating it, and all charges will be automatically refunded.
Does Comet integrate with the other vendors in my tech stack?
+Comet supports a wide array of integration partnerships with industry-leading vendors, including AWS, Google Cloud Storage, Microsoft Azure, Backblaze, Wasabi, and all S3-compatible storage providers. We also have RMM, billing and reporting partners.
For a full list visit our Integration’s page.
I’m looking to lift workload. How will Comet save my team time?
+These are the Top 5 efficiency features that the Comet community has told us they love:
- You can add users in bulk.
- Speed up onboarding by automatically applying policies and auto requesting a user’s first storage vault when you create their profile. Set default retention, schedules, or protected items with policies that apply to multiple people or organizations.
- No need to remotely login to an endpoint. You can live browse, select files and edit everything in the client from the server to run backups and restores remotely.
- Simple two-click process to bulk update all of your agents.
- Build and customize email reports to meet your needs.
Does Comet support GDPR and HIPAA compliance?
+Yes, Comet does not place any restrictions on the files you select for backup. You can also use wildcards and regular-expressions to find files for backup (e.g. all *.docx files on C:\].
You can back up files as large as you like, including large database or zip files. As a best practice, we recommend using other specific Protected Item types if Comet has a more specific integration available, such as the Microsoft SQL Server booster.